How Do You Spot a Fake Email?

(excerpted from an article at eero.com)
Phishing – a fraudulent attempt to obtain your sensitive information by disguising oneself as trustworthy – continues to be one of the most prevalent ways for hackers to gain access to your accounts and compromise your identity.
At the end of 2019, over 86,000 phishing websites were discovered per month. Here are six common signs you are reading a phishing email. Here is an example:
1. Sense of Urgency
While phishers are not limited in who they try to imitate, they often try to copy financial institutions, cloud logins (Apple, Microsoft, Google), or disaster relief organizations. Their goal is an obvious one – to get you to take action on the email. To do so, they inspire a sense of urgency by telling you your funds are at risk, your account is being closed, or some other impending negative action.
2. Suspicious Sender Address
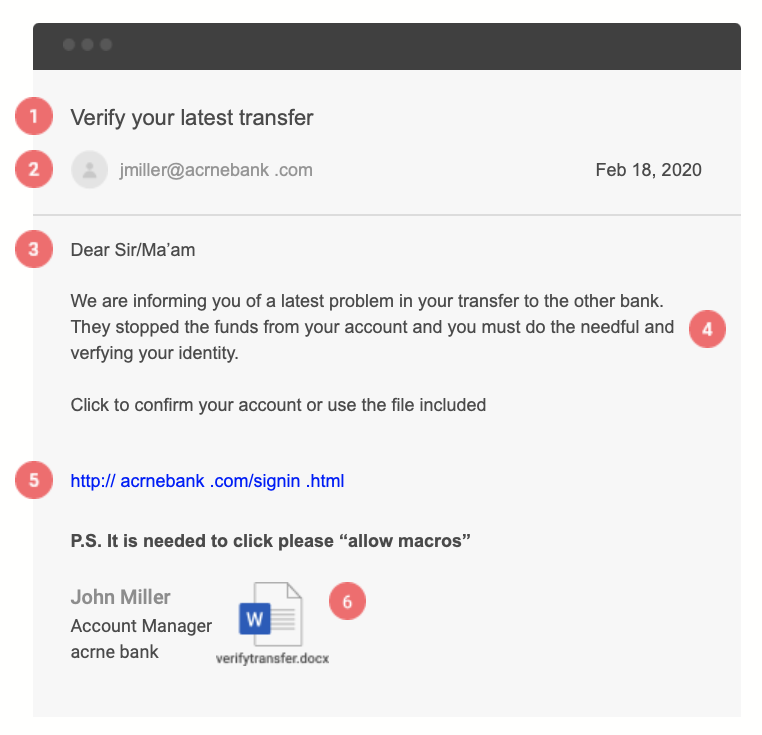
Email applications can only go so far to protect you from phishing. Scammers will often buy a domain name similar to the one they are trying to spoof. In the above example, the fisher is trying to imitate acmebank.com. They opted to use acrnebank.com hoping that your eye would be tricked by using “rn” instead of “m”.
3. Generic Greeting
In an era where marketing is personalized, it is less common to receive an email with a generic salutation. Most trusted institutions will address you by name, especially when an action is required.
4. Spelling and Grammar Mistakes
Spelling and grammar mistakes are a telltale sign of a phishing attempt. Reputable companies proofread communications before publishing. Run-on sentences, misspelled words, and odd phrases are all signs that the email is not legitimate.
5. Link to Invalid Domain
The aim of a phishing attempt is to collect sensitive information. A common way scammers do this is by redirecting you to a fake online form. The link title and where the link takes you will often be different. It is simple to make a link “look” legitimate.
6. Suspicious Attachments
A more nefarious tactic is to attach infected files that allow attackers to gain a foothold into the system. Instead of simply gaining access to one account, the phisher now has to access to the entire computer. They can use their access to target your contacts from your email address. Common file types used include .pdf, .doc/.docx, and .exe files. However, attack techniques are always evolving.
How you can defeat phishing
- Notice how you felt when you initially read the questionable email. If something felt off, then it probably is.
- You can always go to the targeted site manually, i.e. go to your browser and type in www.acmebank.com, and do not click on a link embedded in the email.
- Reach out to a professional or technical friend to get a second opinion if the email seems wrong.
Phishers use a combination of social engineering tools to trick you into doing what they want, and many of them are very good at it. Moreover, many of them target retirement-age individuals, who tend to trust what they read more than younger people do.
If you receive an email that looks suspicious, contact us and we’ll happy to take a look at it for you. We are here to help!